- Identity Jedi Newsletter
- Posts
- The 80th Edition of the Identity Jedi Newsletter
The 80th Edition of the Identity Jedi Newsletter
Non-Human Identity is a thing, Healthcare and Cybersecurity, and Identity Jedi University

Scale your GRC program with Automation and AI
Spending hours gathering evidence, tracking risk, and answering security questionnaires? Move away from manual work by automating key GRC program needs with Vanta.
Automate evidence collection across 21+ frameworks including SOC 2 and ISO 27001 with continuous monitoring
Centralize risk and report on program impact to internal teams
Create your own Trust Center to proactively manage buyer needs
Leverage AI to answer security questionnaires faster
Over 7,000 global companies like Atlassian, Flo Health, and Quora use Vanta to build trust and prove security in real time. Connect with a team member to learn more.
Hey Jedi welcome to the 80th edition of the Identity Jedi Newsletter! Wow, big number 80, and we are zooming right along! Once again, a big shoutout to Vanta for sponsoring this week’s newsletter edition; we love their partnership! Be sure to check them out!
This week’s edition includes a word about Non-Human Identity, the state of cybersecurity in Healthcare, and some IDJ University updates. In a shocking twist, no one bought a company this week…lol
This week's edition

Still have a long way to go..
Every company is a tech company, and every company has to manage cybersecurity. Tis the way of the world.
TL;DR: The GAO made 1,610 in 2010, 567 remain unimplemented.
Yup, that sounds about right.
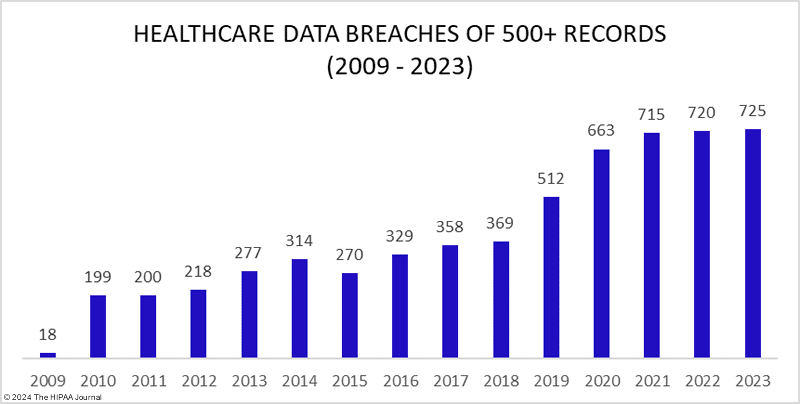
Healthcare needs a band-aid and a bourbon.
An eye-opening look at the state of cybersecurity in healthcare. More on this later..

These ARE the droids you are looking for..
Here's a fun fact, albeit a bit terrifying: 83 percent of web traffic is generated via APIs. Yes, you read that right—83%. This statistic highlights a significant shift in how the web operates and underscores the growing influence of APIs in our digital world. What does this mean for us? Essentially, just about everything you see as web traffic is conducted through APIs. And here's another startling revelation: it's not humans generating this traffic. Instead, non-human accounts are the primary contributors. These non-human accounts aren't just passive data collectors. They're actively connecting to other apps and services, exchanging data at an unprecedented rate. Many of these connections are facilitated by long-lasting tokens—some created years ago—that remain active and continuously connecting.
If you think non-human identities aren't an issue for your organization, think again. This phenomenon is one of the next significant challenges we must tackle as both identity practitioners and security professionals. We need to devise strategies to manage and govern these non-human entities effectively.Historically, identity and security measures were centered around human users. However, with non-human accounts now dominating web traffic, we must expand these practices. The same identity and security protocols we’ve applied to human accounts must now encompass all entities in our digital ecosystems.
The sheer volume of API-generated web traffic underscores the need for a paradigm shift in how we handle digital identities and security. As we move forward, addressing these challenges will be crucial in maintaining the integrity and security of our digital infrastructure.
Let's not treat this like we did privileged access management and sweep it under the rug. This problem moves too fast, and the scale will be too big before you know it.


Identity Jedi Show Podcast
The Last Word
I’m concerned about our Healthcare system for various reasons, but in this specific instance, when it comes to cybersecurity. Some “fun” stats to consider:
74% of ransomware attacks are targeted at hospitals
88% of healthcare workers reportedly open phishing emails.
Less than 6% of the budget in healthcare organizations goes towards cybersecurity.
Ok so what do we do here? I know Healthcare, much like HigherEd, is its own beast when it comes to implementing things. But we have to look seriously at this and find ways to help them improve. Better open-source tools with easier implementation? With all the advancements we’ve been making with new tools in Identity, could we not open-source some of these? Food for thought, but we should talk about this more.
Identity Jedi University ( Beta)
Ok, so Identity Jedi Univesity is almost complete, and the first course is done! I’m taking everything that I’ve learned in my career and turning them into actionable courses that you can use. And of course, you know I’m planning a big launch for it. So I want to ensure you all get access to the waitlist. Be on the lookout for an email with a link for registration. Premium subscribers you’ll be getting a separate email,as you'll be getting instant early access!
I can’t wait!
Till next time folks.
Be Good to each other, Be Kind to each other, Love each other
-Identity Jedi
What did you think of this weeks newsletter? |










Reply